It's not the one-time heist you should fear. It's the slow leak of 'just one box' repeated 1,000 times. A pallet of laptops disappearing overnight makes headlines. A single unit missing every week for a year? That's invisible—until your annual count reveals a $50,000 black hole.
Employee theft is the silent drain on inventory accuracy and profitability. In 2022, U.S. retailers lost $112.1 billion to shrinkage, and employee theft accounted for 28.5% of that—nearly $27 billion. But here's the paradox: the most effective prevention strategies don't involve cameras in every corner or treating your team like criminals. They involve smart systems, trust, and unpredictability.
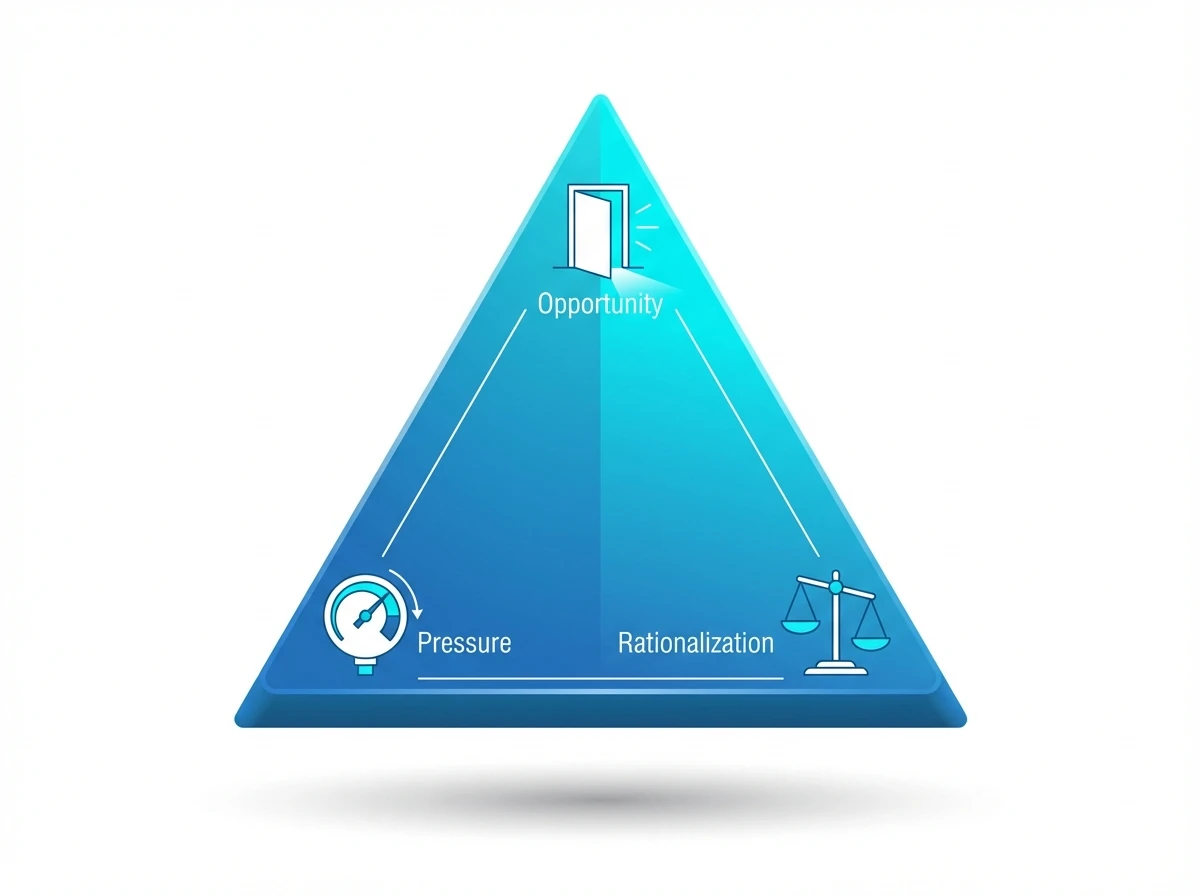
Why Good People Steal: The Fraud Triangle
Most employee theft isn't committed by career criminals. It's committed by ordinary people facing the right combination of three factors, known as the Fraud Triangle:
Financial stress (medical bills, debt, low wages) creates a motive. Retail and warehouse workers may feel underpaid relative to the value they handle daily.
Weak controls make theft easy. If there are no cameras in the warehouse, no cycle counts, and no separation of duties, the opportunity is wide open.
Employees justify the act. 'The company can afford it.' 'I'm just taking what I'm owed.' 'Everyone does it.' Once they rationalize it, the mental barrier is gone.
Studies show that 80% of people might commit fraud given the right combination of pressure, opportunity, and rationalization. Your job isn't to assume everyone is a thief. Your job is to collapse the triangle by removing opportunity and making rationalization impossible.
The Anatomy of the Leak
Employee theft rarely looks like a Hollywood heist. It looks like this:
- A picker grabs an extra unit 'for a friend' during their shift.
- A receiving clerk marks a shipment as damaged when it's perfect, then takes it home.
- A supervisor voids a transaction and pockets the item.
- Someone walks out with small, high-value items (cosmetics, electronics, tools) that are easy to conceal.
The pattern is gradual and mimics normal activity. That's why traditional security measures—cameras, guards, bag checks—often miss it. You need systematic controls that catch discrepancies before they become disasters.
Strategy 1: Build Trust, Not a Surveillance State
The foundation of theft prevention isn't technology. It's culture. Employees who feel valued, respected, and fairly compensated are less likely to steal. But culture doesn't mean naïveté—it means smart design.
Cultural Controls That Work
- Pay fairly.Low wages are a rationalization factory. If you handle $100,000 in inventory daily and make $15/hour, resentment builds.
- Recognize good work.Employees who feel invisible are more likely to justify theft. Visibility and recognition reduce rationalization.
- Communicate expectations clearly.Make it clear from day one: theft is termination, no exceptions. No gray area.
- Lead by example.If managers bend the rules, employees will too. Integrity starts at the top.
A positive work environment reduces job dissatisfaction—a common driver of theft. But culture alone isn't enough. You need systems.
Strategy 2: Use Technology as a Silent Partner
The best theft prevention tools don't feel like surveillance. They feel like efficiency upgrades that happen to create audit trails.
Barcode Scanning: The Invisible Deterrent
Barcode scanners track every movement. Receiving, putaway, picking, packing—every scan creates a timestamped record tied to a user ID. This does two things:
- Deters opportunistic theft: Employees know their actions are logged. The 'invisible box grab' becomes risky.
- Exposes patterns: If the same employee consistently has variances in their zone, you have a lead.
Barcode systems aren't about watching people. They're about knowing what moved, when, and by whom—so discrepancies trigger questions, not accusations.
Blind Counts: Remove the Temptation to Fudge
A blind count means the counter doesn't see the system's expected quantity. They count what they see, period. This eliminates confirmation bias and makes it harder to 'adjust' numbers to hide theft.
Best practice: use two-person teams for blind counts. One counts, one verifies. If both are stealing together, you have bigger problems—but that's rare.
Rotate your counting teams. Don't let the same person count the same zone every week. Randomness disrupts collusion and prevents employees from learning 'safe' times to act.
Access Controls: Limit Who Touches What
Not everyone needs access to everything. Use role-based access controls:
- Pickers can pick, but can't void transactions.
- Receiving clerks can log shipments, but can't adjust inventory without manager approval.
- High-value zones (electronics, jewelry, tools) require manager badge access.
Access control isn't about distrust. It's about separation of duties—a fundamental control that prevents any single person from having end-to-end power over a transaction.
Strategy 3: The Power of Randomness
Predictability is the enemy of theft prevention. If employees know you count Aisle A every Monday and never touch Aisle D, guess where the leaks happen?
Random Cycle Counts: The Security Camera That Never Blinks
Regular cycle counting acts as a deterrent because it's unpredictable. Employees don't know when their zone will be counted, so the risk of getting caught is constant.
Randomness Best Practices
- Randomize the schedule.Don't count the same zones at the same time every week.
- Randomize the counter.If an employee doesn't normally work in a zone, assign them to count it. Fresh eyes catch more.
- Count outside business hours occasionally.If theft happens after closing, a surprise weekend audit will expose it.
Organizations that conduct surprise audits report a median loss of $75,000, compared to $200,000 for those that don't—a 63% reduction. Fraud schemes in organizations without surprise audits go undetected for 18 months on average. With surprise audits? Nine months.
Unpredictability prevents thieves from covering their tracks. They can't destroy records, alter logs, or hide evidence if they don't know the audit is coming.
Strategy 4: Create Safe Channels for Reporting
Most employees aren't thieves. And many of them know who is. But they won't speak up if they fear retaliation or don't trust management to act. That's where anonymous reporting comes in.
Anonymous Hotlines and Digital Channels
Whistleblower hotlines protect the anonymity of employees who report theft, fraud, harassment, or safety violations. Studies show that whistleblowers uncover more than twice the fraud that professional auditors catch.
Implementation tips:
- Use a third-party service (e.g., 1-800 hotlines or web portals) to ensure true anonymity.
- Promote the hotline in break rooms, onboarding materials, and employee handbooks.
- Investigate every report promptly and communicate (without revealing details) that reports are taken seriously.
- Never retaliate. One act of retaliation will kill trust and shut down reporting forever.
When employees know there's a safe way to report concerns, the culture shifts from 'everyone looks the other way' to 'we hold each other accountable.' That shift is worth more than any security camera.
Strategy 5: Measure What Matters
You can't improve what you don't measure. Track these KPIs to know if your theft prevention strategies are working:
Calculate: (Recorded Inventory - Actual Inventory) / Recorded Inventory. Track monthly. A rising rate signals a problem.
Which aisles or departments show the highest discrepancies? Focus prevention efforts there.
If the same employee's zone consistently shows shortages, investigate. It might be process failure—or theft.
Are you completing counts on schedule? If compliance drops, so does deterrence.
What percentage of your inventory matches system records? Aim for 98%+. Anything lower invites theft and operational chaos.
Review these metrics quarterly with your leadership team. Look for patterns. A single variance is a data point. A trend is a signal.
The Monday Morning Action Plan
You don't need to overhaul your operation overnight. Start with these three actions this week:
This Week's To-Do
- Implement blind counts.Pick one zone. Count it blind. Compare to system. Investigate any variance over 2%.
- Randomize one cycle count.Don't announce it. Pick a zone that hasn't been counted in a while. Use a different counter than usual.
- Review your shrinkage rate.Calculate it for last month. If it's over 1.5%, dig into the variances by zone and shift.
Then, over the next 90 days:
- Set up an anonymous reporting channel (even a simple Google Form with no required email works as a start).
- Review access controls: who can void transactions? Who can adjust inventory? Tighten permissions.
- Train your team on the new counting procedures and explain why they matter (accuracy, not surveillance).
Conclusion: Trust, but Verify
The goal isn't to catch thieves. The goal is to make theft so difficult, risky, and unpredictable that it doesn't happen in the first place. You do that by removing opportunity, creating accountability, and building a culture where theft isn't rationalized away.
Most of your team is honest. Treat them that way. But design your systems as if everyone might slip—because under the right pressure, anyone might. The fraud triangle collapses when you remove opportunity. Remove opportunity, and you stop the leak.
Start this week. Count blind. Count random. Measure the variance. And watch the slow leak turn into a trickle, then stop.
